Security is never static. New cyber attacks, misconfigurations, and security products are rampant. How do you take control of an ever-changing threat landscape?
The only way to know is to test your own defenses before hackers can.
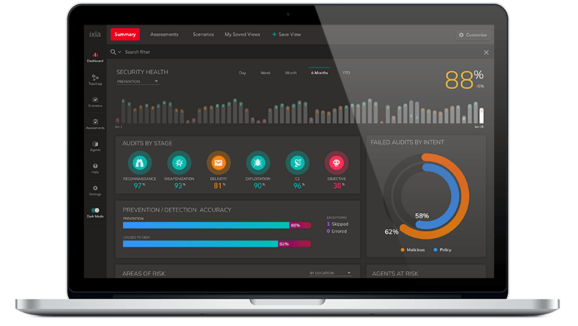
Threat Simulator is a breach and attack simulation (BAS) platform built on 20+ years of leadership in network security testing.
SecOps teams trust Threat Simulator to not only simulate the cyber attack kill-chain, but also to analyze security spend and deliver dynamic remediation recommendations to:

Optimize security posture and empower SecOps by staying ahead of attackers
Reduce SecOps alert fatigue and block up to 80% of malicious traffic

Let’s face it: simply buying and plugging in a new security device is not going to magically make problems disappear. You don’t need another defensive tool — you need to know how effective the tools you have actually are.
According to our research, nearly 2 in 3 companies aren’t confident their security tools are configured and defending properly. That’s why so many SecOps teams rely on breach and attack simulation (BAS) tools like Threat Simulator.
By continuously simulating real-world attacks on your live network, you can emulate the entire cyber attack kill chain with maximum confidence and zero risk — validating the strength of your defenses, identifying potential cyber security threats, and remediating gaps all at once.
Let’s face it: simply buying and plugging in a new security device is not going to magically make problems disappear. You don’t need another defensive tool — you need to know how effective the tools you have actually are.
According to our research, nearly 2 in 3 companies aren’t confident their security tools are configured and defending properly. That’s why so many SecOps teams rely on breach and attack simulation (BAS) tools like Threat Simulator.
By continuously simulating real-world attacks on your live network, you can emulate the entire cyber attack kill chain with maximum confidence and zero risk — validating the strength of your defenses, identifying potential cyber security threats, and remediating gaps all at once.
The world leader in application and security testing, our Application and Threat Intelligence (ATI) Research Center keeps Threat Simulator updated with the latest threats. Our database contains more than 50 million records, and millions of new threats are analyzed and cataloged each month.
With continuous updates from our feed, you’ll always be able to emulate the latest cyber security threats and attacks. But curtailing threats also means knowing your enemy. So, when you need to dive a little deeper, you can drill down on specific attacks to learn even more. From cyber attack signatures to evidence of malicious activity, our database makes it easy to leave no stone unturned.